Before being executed for his crimes, the galactic pirate Gold D Adler reportedly said the words : “You want my treasure? You can have it! I left everything I gathered together in one place! Now you just have to find it!” With these words, a new page has appeared on his personal site. It’s up to you!
The validation flag is like HACKDAY{1a79a4d60de6718e8e5b326e338ae533}
Table of contents:
Recon & enumeration
I firstly performed a nmap scan to understand the target.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
nmap -sV -T4 7c21111516t.hackday.fr
Starting Nmap 7.92 ( https://nmap.org ) at 2023-03-17 19:36 CET
Nmap scan report for 7c21111516t.hackday.fr (193.70.90.113)
Host is up (0.44s latency).
rDNS record for 193.70.90.113: vps-130fe7f4.vps.ovh.net
Not shown: 983 filtered tcp ports (no-response), 14 filtered tcp ports (host-unreach)
PORT STATE SERVICE VERSION
80/tcp open http
443/tcp open tcpwrapped
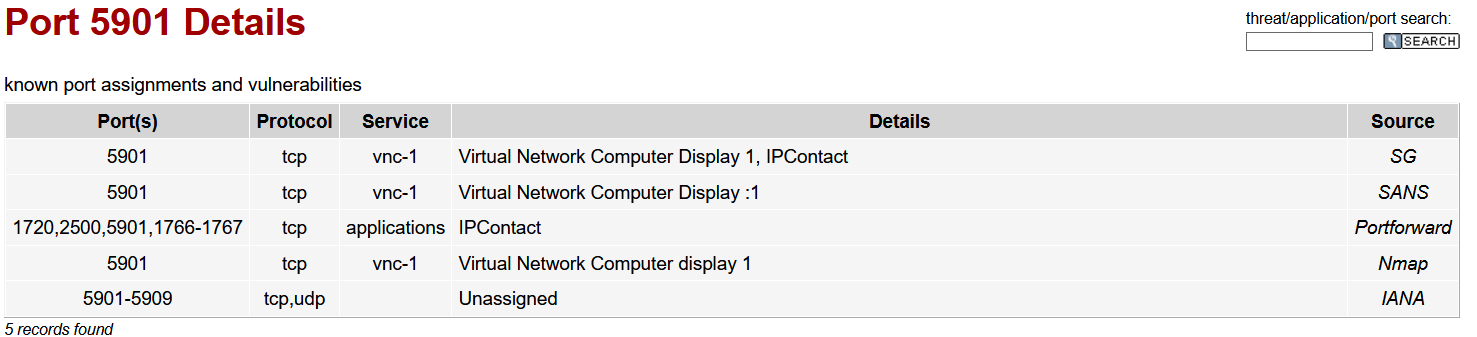
5901/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.92%I=7%D=3/17%Time=6414BC44%P=x86_64-pc-linux-gnu%r(GetR
SF:equest,91,"HTTP/1\.0\x20302\x20Found\r\nLocation:\x20https:///\r\nDate:
SF:\x20Fri,\x2017\x20Mar\x202023\x2019:15:16\x20GMT\r\nContent-Length:\x20
SF:5\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\n\r\nFound")%r(HTT
SF:POptions,AC,"HTTP/1\.0\x20307\x20Temporary\x20Redirect\r\nLocation:\x20
SF:https:///\r\nDate:\x20Fri,\x2017\x20Mar\x202023\x2019:15:16\x20GMT\r\nC
SF:ontent-Length:\x2018\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r
SF:\n\r\nTemporary\x20Redirect");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2353.58 seconds
So, we have a web server and something on port 5901. I didn’t know this port, so I did some research and found this:
So probably a VNC server on this port.
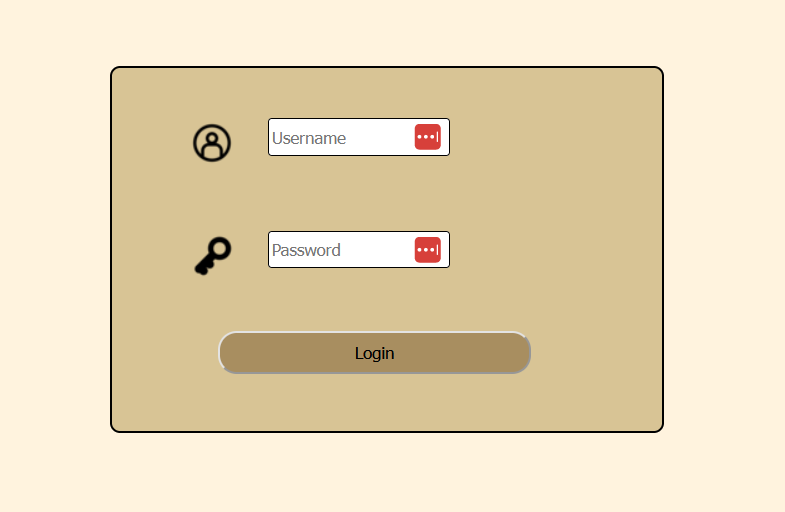
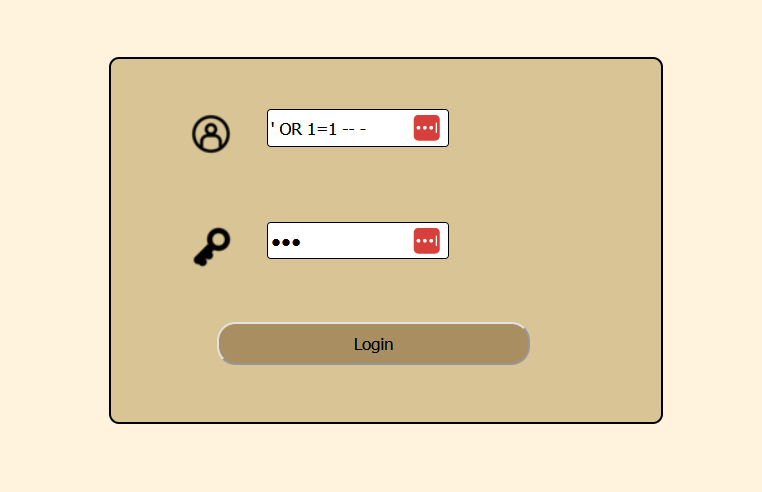
By reaching the website, we arrived on an index.php page, containing a login form.
Well-known files
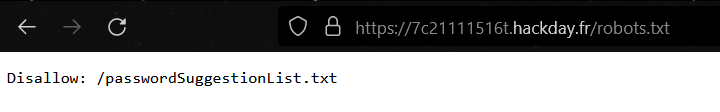
I continued my recon phase and looked for well-known files and successfully get a /robots.txt
And we get the following content:
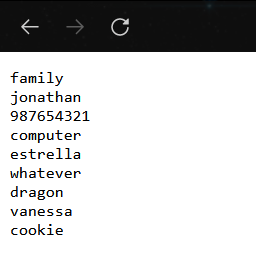
Here, my first idea was to try to connect to the login form with a combo of user/password from this suggestion list. So, I wrote a python script, but i didn’t get connected.
Exploitation
In this case, my next idea was to try an SQL injection
SQL Injection
And it worked !
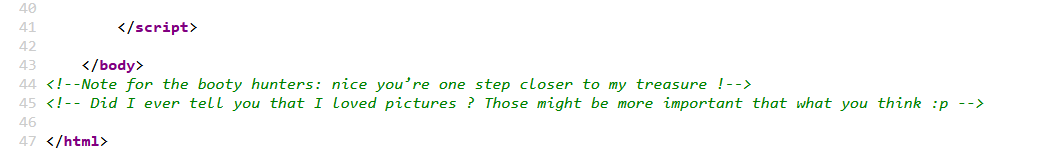
Now, we arrived on a page with a slider of 30 images. We don’t find anything interesting on the images, so I decided to check the source code and found an interesting comment:
Steganography
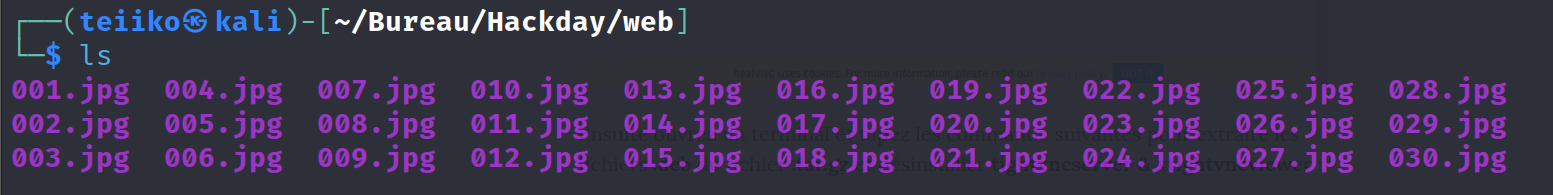
Here, we understand that there is probably hidden data in images. My first intention was to check the highest size image but i didn’t get any usefull information. So, I understood I’ll have to check all images. In order to not download and try all images one by one, i used the following oneliner to win time:
for i in {1..30}; do wget https://7c21111516t.hackday.fr/images/slides/$(printf "%03d" "$i").jpg; done
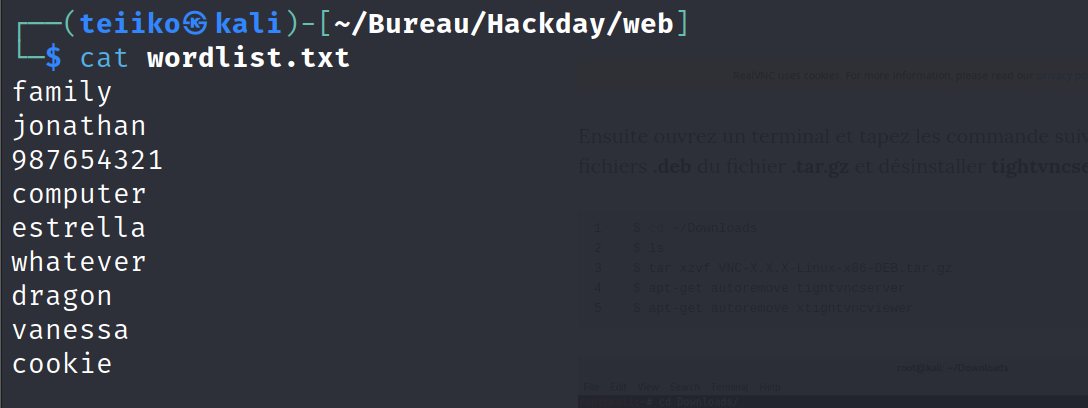
Then, I created a wordlist file containing data found in /passwordSuggestionList.txt
Steghide
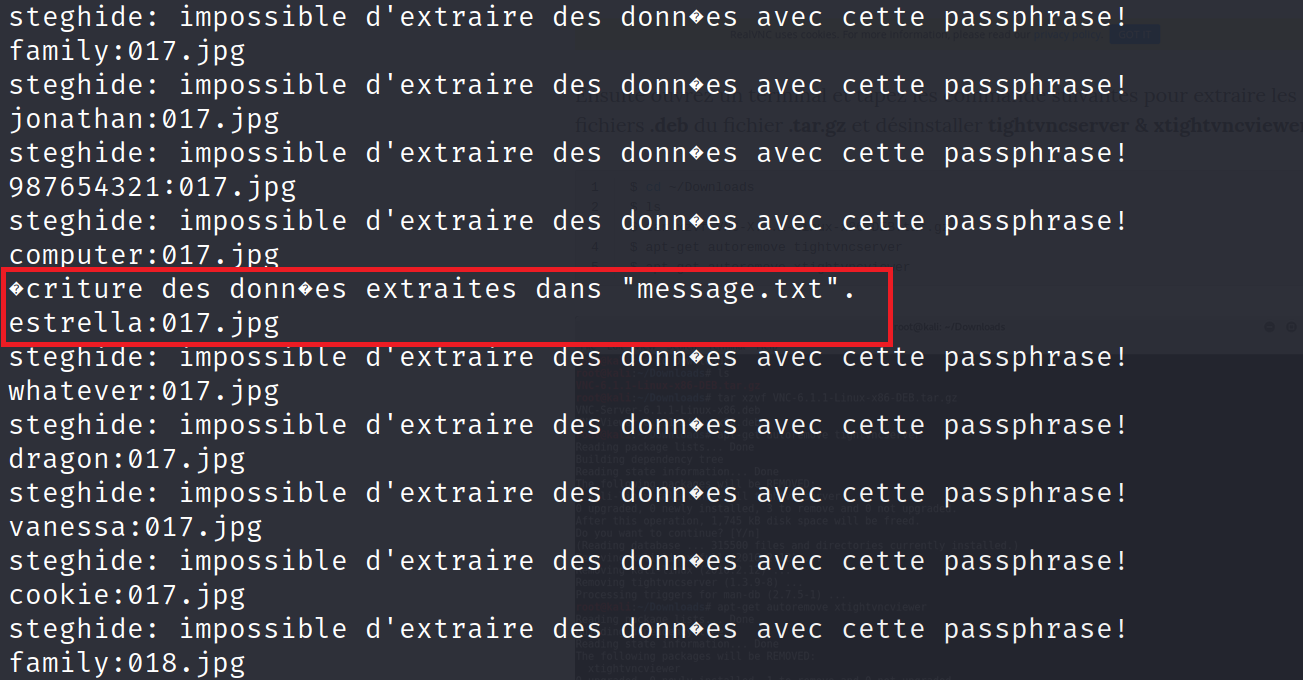
Once all images are dowloaded, i used the following oneliner in order to perform a steghide extract by trying all passwords for each image.
for file in *.jpg; do for pass in $(cat wordlist.txt); do steghide extract -p "$pass" -sf "$file"; echo "$pass:$file"; done; done
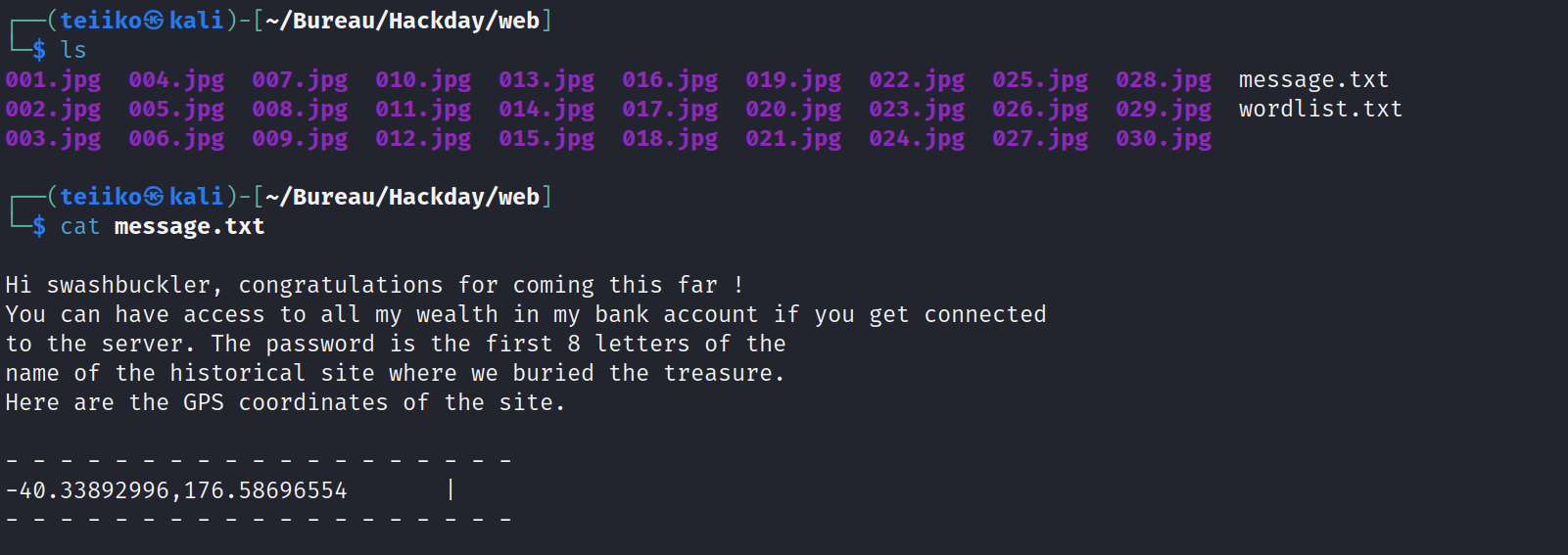
We found a hidden file in 017.jpg with estrella as passphrase.
Let’s do some GEOINT with GPS coordinates.
GEOINT
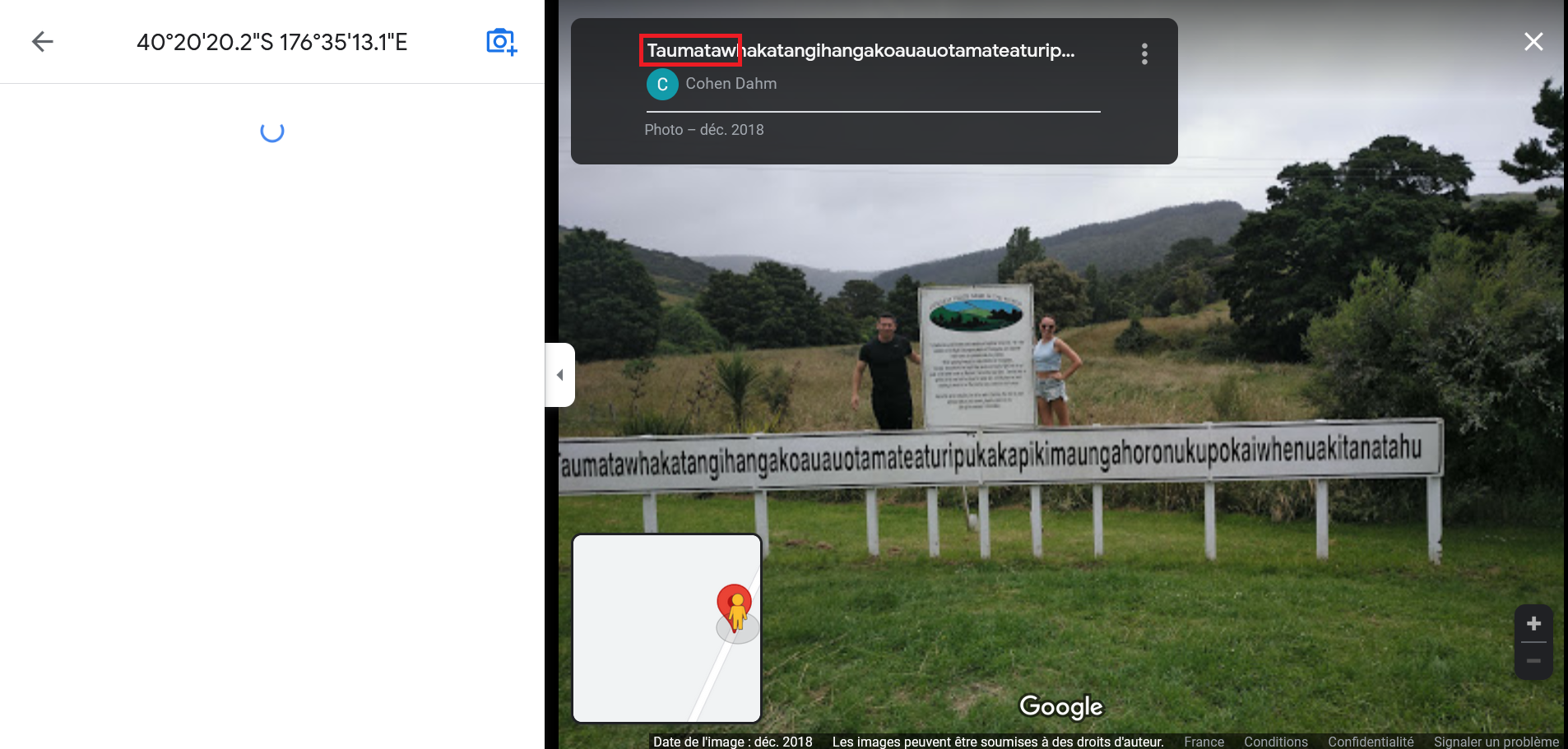
By pasting coordinates in Google Maps, we arrived on a site in New-Zealand with the longest place name in the world:
Taumatawhakatangihangakoauauotamateaturipukakapikimaungahoronukupokaiwhenuakitanatahu
By extracting first 8 characters, we get Taumataw
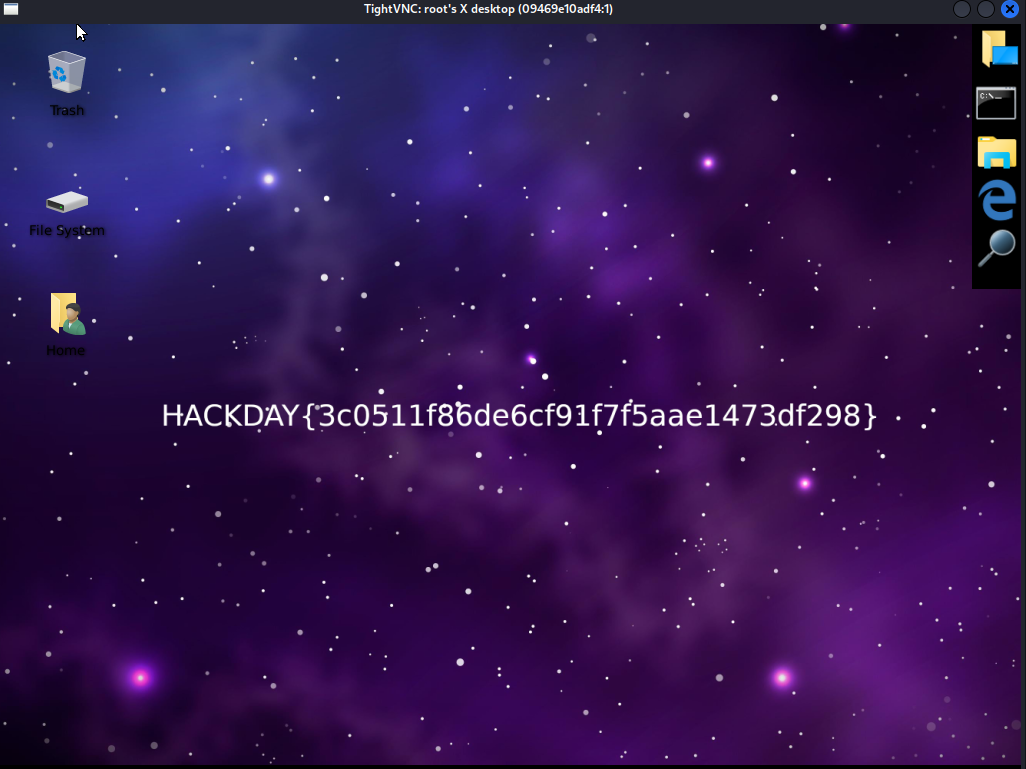
At this moment, i tried a lot of things with this password and I didn’t get anything usefull. But my team mate finally found the flag by trying to connect to the VNC server with vncviewer.
Flag
And we got the flag !
🚩
HACKDAY{3c0511f86de6cf91f7f5aae1473df298}
Thanks for reading ! You can give me a feedback on Discord - Teiiko#8831