You just found a website with a new concept: do not store anything in a database, and do not let user to chose their password.
All stored data are volatile, and will be cleaned everyday. To register an account, you just have to put a username, and the website will generate you a password according to your username. Once an account is create, the username is locked for you, so you will be the only one to access your data.
Find how the website generate passwords, and take over admin account to view all his secrets
Bruteforce is useless!
Table of contents:
Introduction
After reading challenge description, we understand that we have to find a way to connect as admin by playing with the password generation pattern.
Recon phase
Once accessing to the website, we arrived on the main page showing a login form and a register form.
So let’s start creating an account to see how works the app. By carefully looking at the form, we notice that the “password” field is disabled, indicating that the password is auto-generated. In this case, I’ll create an acount with the username teiiko
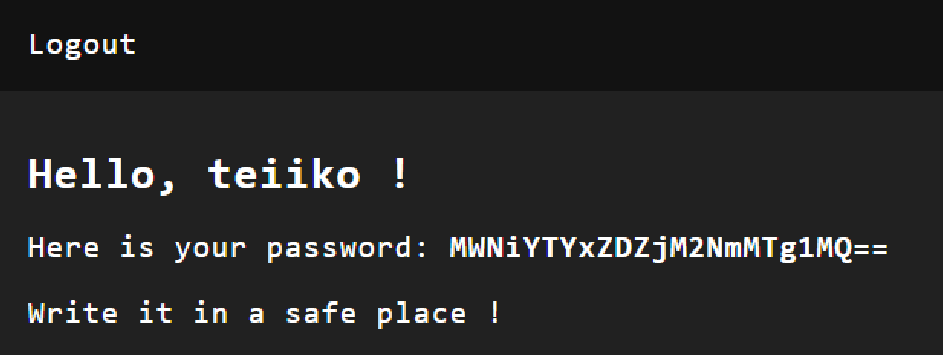
When created, we are redirected to our profile page, showing us our password.
MWNiYTYxZDZjM2NmMTg1MQ==
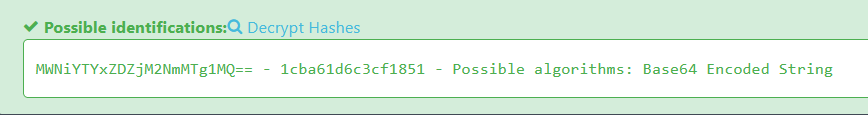
We recognize that it is a base64-encoded string. We can verify this by passing the string through the hash identifier tool (cf: Hash identifier)
Unsurprisingly, it is indeed a base64-encoded string. The tool also returns the decoded value: 1cba61d6c3cf1851.
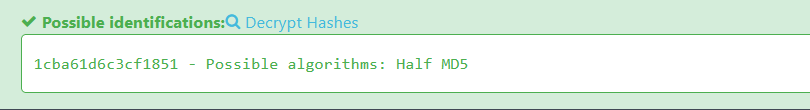
Similarly, we can pass this string in the same tool to determine the encoding used.
Now, we understand that our password is encoded with Half-MD5 algorithm.
Guessing
This is where the guessing part comes in. Indeed, after much research, it is difficult to find information about half md5. According to the statement, we know that our generated password is related to our username.
Here, my idea was to encrypt my username in md5, in order to find data related to our half md5 hash.
I used https://md5decrypt.net/ and get b5e4a5d71cba61d6c3cf18519bae825c.
In this case, we have:
md5('teiiko') = b5e4a5d71cba61d6c3cf18519bae825chalf_md5('teiiko') = 1cba61d6c3cf1851
With a little attention, we notice that our HalfMD5 is included in the full MD5 hash of our username, with 8 characters on each side:
Now, we just have to exploit this vuln to get access to admin account.
Exploitation phase
To exploit this vuln, we first have to extract the half md5 from the md5-encoded string ‘admin’.
- Extract half md5
Full md5 = 21232f297a57a5a743894a0e4a801fc3 → Half md5 = 7a57a5a743894a0e
- Base64-encoded string
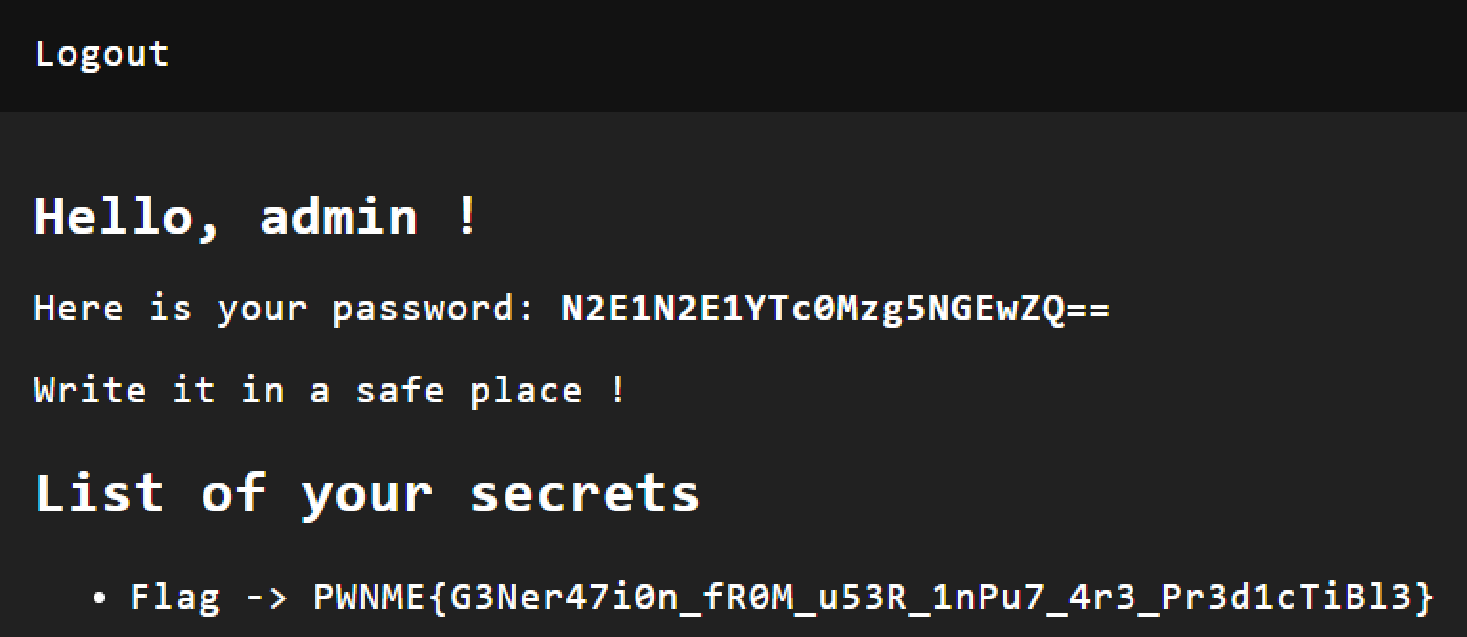
Finally, we have base64(half_md5('admin')) = N2E1N2E1YTc0Mzg5NGEwZQo=.
We can now go back to main page, and log in as admin !
Flag
🚩
PWNME{G3Ner47i0n_fR0M_u53R_1nPu7_4r3_Pr3d1cTiBl3}
Thanks for reading ! Give me a feedback on Discord - Teiiko#8831